According to a recent study conducted by SANS Institute, Phishing accounts for 90% of Data breaches in Cybersecurity. Effects of a successful phishing attack can be catastrophic to a business. Contrary to popular belief that many organizations are too small to warrant attention from attackers, both large and smaller organizations are susceptible to phishing attacks.
In most cases, smaller organizations fall victim to phishing attacks as they may not have the resources to build sophisticated security networks or awareness schemes to prevent their staff from falling for the scams.
What is phishing?
It is a form of social engineering that cybercriminals attempt to get sensitive data or information from people like their usernames, passwords, financial information or credit card details, by disguising as someone trustworthy. But like everything else in the technology, phishing scams are rapidly evolving both in terms of the tools being used and the cleverness with which they are being designed.
The most common phishing techniques include:
- Deceptive phishing: It is the most common phishing scam where the attacker impersonates a legitimate company in an attempt to steal users’ personal data
- Spear phishing: It is a targeted attempt to steal sensitive information such as account credentials or financial information from a specific victim. Symantec’s Internet Security Threat Report 2019 shows spear-phishing emails are employed by almost two-thirds (65 per cent) of all known groups completing targeted cyber-attacks. The report also tells us that 96 per cent of targeted attacks are carried out for the purpose of intelligence gathering.
- Whaling: In general, phishing efforts are focused on collecting personal data about users. In whaling, the targets are high-ranking persons in the organization, executives or others in powerful positions or job titles.
- CEO Fraud: This involves the impersonation of a company’s CEO or high ranking official to try and trick an employee into wire transferring company money, for supposedly legitimate business reasons. During CEO fraud attacks, email spoofing –the forgery of an email header and sender address so that messages appear to have originated from someone- is often used.
- Vishing: It is a form of phishing where the attacker uses a phone call to solicit information from the victim.
- Smishing: Just like phishing, smishing uses cell phone text messages to lure victims in. Often the text will contain an URL or telephone number. The telephone number often has an automatic voice response system. And again, a bit like phishing, the smishing message usually asks for your immediate attention.
- Clone phishing: Clone phishing is a phishing attack whereby a legitimate, and previously delivered, an email containing an attachment or link has had its content and recipient address taken and want to create an almost identical or cloned email. The attachment or link within the e-mail is replaced with a malicious version then sent from an email address spoofed to seem to return from the first sender. It may claim to be a resend of the first or an updated version to the first. Typically, this needs either the sender or recipient to possess been previously hacked for the malicious third party to get the legitimate email.
- Pharming: It is a cyber-attack which redirects traffic from a legitimate website to another, fake site. This typically involves corruption in DNS server software or the targeting of a local network router.
How to protect against phishing attacks
Here are steps you can take today to protect yourself from phishing attacks.
Conduct Employee Security Awareness Training
For an organization, the human firewall is the first line of defence therefore organizations should conduct employee security awareness training. Phishing awareness training program educates employees on how to detect and report phishing attempts.
For a deceptive phish to be successful it depends on how closely the attack email resembles a legitimate email. Therefore, users should be trained to inspect all links carefully to see if they redirect to an unknown or suspicious website. They should also look out for generic salutations, grammar mistakes and spelling errors scattered throughout the e-mail.
Employees should also be discouraged from posting sensitive personal or corporate information on social media.
Conduct phishing simulations
Phishing simulations can also be used as part of employee training. This can assist the organization to assess the effectiveness of awareness training. Through phishing simulations, employees learn spotting phishing tactics and more employees get caught on the phishing hook during a simulation, the less likely they are to forget the lesson.
Use of Email Security Solutions
Invest in email security solutions to analyze inbound emails for the presence of any malicious links or attachments. Current email security software leverage on Artificial Intelligence technology to provide the best predictive security that inspects the reputation of the website of attached URLs before delivery. They also provide email sandboxing technology as an extra layer of protection that blocks unwanted applications and prevent zero-day malware from reaching the organization’s network.
Email security solutions may keep many phishing emails out of your inbox but scammers are always trying to outsmart them, so it’s a good idea to add extra layers of protection such as employee awareness training.
What to look out for?
Below are the social engineering flags to look out for:
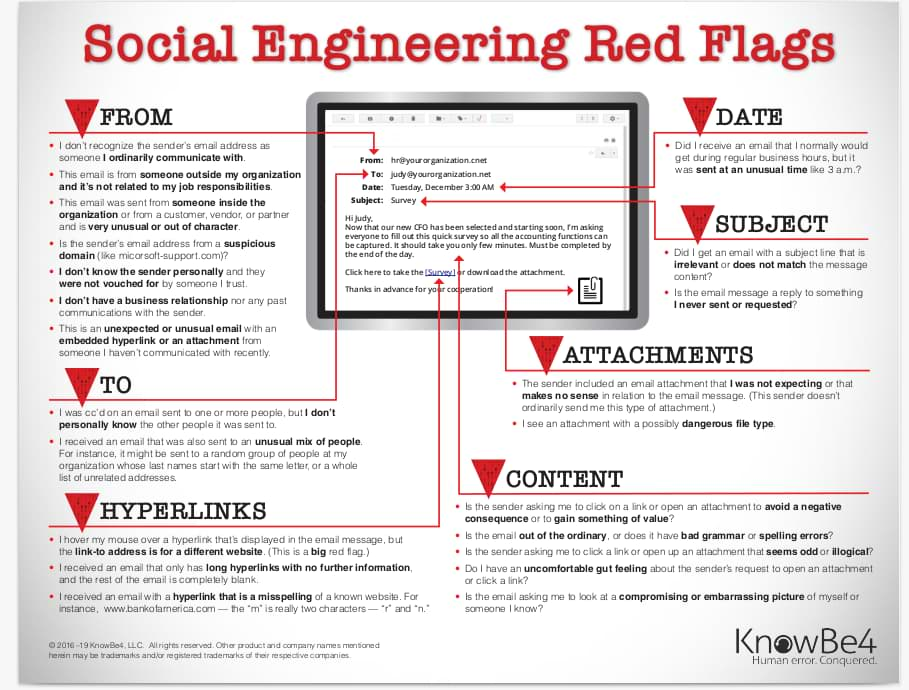
Image credits for KnowBe4.com

