The security skills gap is real. Any CISO from any company in the world from any business domain will tell you that his or her biggest challenge is hiring security staff followed by keeping that security staff on the payroll. The market supply and demand scales are heavily tipped on the demand side and security professionals, especially those with the right skills have no issues finding alternative positions, better paid somewhere else.
Developing security capability is high on the agenda of practically all countries in the world, beginning from the re-skilling of government and corporate security teams up to the development of national security operators, with capacity building programmes covering all age groups, from schools and universities to back-to-civilian-life programmes in the armed forces.
Then came the C19 2020 pandemic, which, still in its prime, has pushed all traditional training and education activities to the deep end having to cope with the impossibility of face-to face-interaction.
The solution to the security skill gap can be summarized as follows:
- Scale – Training and re-skilling millions of security professionals all over the world
- Method – Provision of experiential training to ensure real competencies are developed
- Content – Real-world scenarios to ensure security operators and managers can meet threats.
The industry has been addressing the scale issue for some years now by turning to the development and provision of online training and education. Many universities have put their entire teaching curricula online and countless training providers have begun offering online training webinars, pre-recorded training sessions and self-paced learning materials. Unfortunately, scaling by itself does not solve the problem.
The industry requires professionals with tangible skills, which can only be developed over time through on-the-job experience and that’s where the “method” in training and education plays an important role.
The Method – Experiential Learning
Experiential learning is the process of learning through experience, and is more specifically defined as learning through reflection on doing. Experiential learning covers fundamentally two aspects:
- Development of skills and ability
- Application of those skills in a realistic environment.
A classic example of experiential learning is the one we go through when learning to drive a car. Firstly, we acquire the knowledge we will need to drive a car on public roads. Then we apply such knowledge and skills to test-drive on a public road and, as we practise driving over the years, we become better drivers.
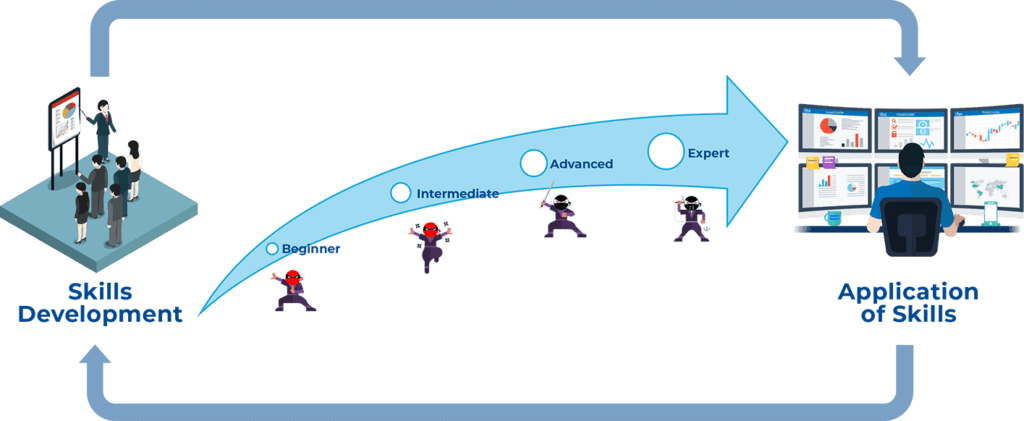
For many years, the security training and education industry has focused on teaching people how to drive through static MS PowerPoint slides and theory examples, giving people only a limited opportunity to develop their skills.
As computer labs and virtualization technology developed, the skills development has become more and more experiential giving students and young professionals the opportunity to experience security tools, technologies and processes and to cement the theoretical concepts and methodologies. Over that last two years, cloud technology has allowed the development of online, fast and cost-effective experiential training accessible to the masses.
Many of such online platforms are promoted as cyber ranges or virtual firing ranges where people can develop and hone their cyber security skills. To a certain extent that is correct. Unfortunately, such cyber ranges only address the first aspect of the experiential learning, i.e., the “Development of Skills”.
From an employer’s perspective, a professional who has been trained this way is like a driver who has been practising only in a parking lot without ever driving on public roads! Surely that is far better than just reading about driving cars and surely having someone with good driving skills is an asset to the company. However, how will he or she cope in a real environment with real threats and dangers where human interaction and teamwork are also required?
That’s where the second aspect of experiential learning comes in, and that is the application of skills and abilities in a realistic environment and the need to test and measure such capability.
Not all Cyber Ranges are created Equal
When it comes to cyber ranges, they currently fall into one of two categories, one focusing on skills development and the other on the application of those skills in a realistic environment.
The former, are mostly online, based on the use of such public cloud providers as Amazon AWS or Microsoft Azure and based on cost-effective subscription models to scale the delivery. The latter are mostly on premises, based on traditional virtualization technology and priced in the hundreds of thousands of dollars for annual licensing. The latter category also includes some providers offering per-use business models where a realistic environment can be set up on demand on a public cloud infrastructure.
The former address the scale aspect of the security skills gap. However, the experiential learning method requires both types of cyber ranges. Professionals need both to develop their skills and to practise such skills in true-to-life environments.
As an example, experiential learning for SOC analysts should cover two aspects:
- Development of the skills to identify and respond to cyber attacks (e.g., traffic analysis, log analysis, writing attack signatures, etc.)
- Applying those skills in a simulated environment that would mimic a real work environment (up to high-fidelity corporate environment replicas or even a digital twin) by making use of security tools against cleverly simulated attacks in order to test SOC analyst proficiency.
Both these aspects of experiential learning are far from static. The security domain is ever changing and so is the required experiential learning with new training modules and realistic simulations being necessarily developed all the time. Every organization would ideally like to count on skilled security professionals, capable to train and deal with real cyber attacks in an environment that is as close as possible to the one they are called to defend every day.
Ultimately, the ability to customize the cyber range simulation environment is paramount to ensure that both aspects of experiential learning are addressed at minimal cost.
The following table outlines the key differences between the two high-level categories of cyber ranges:
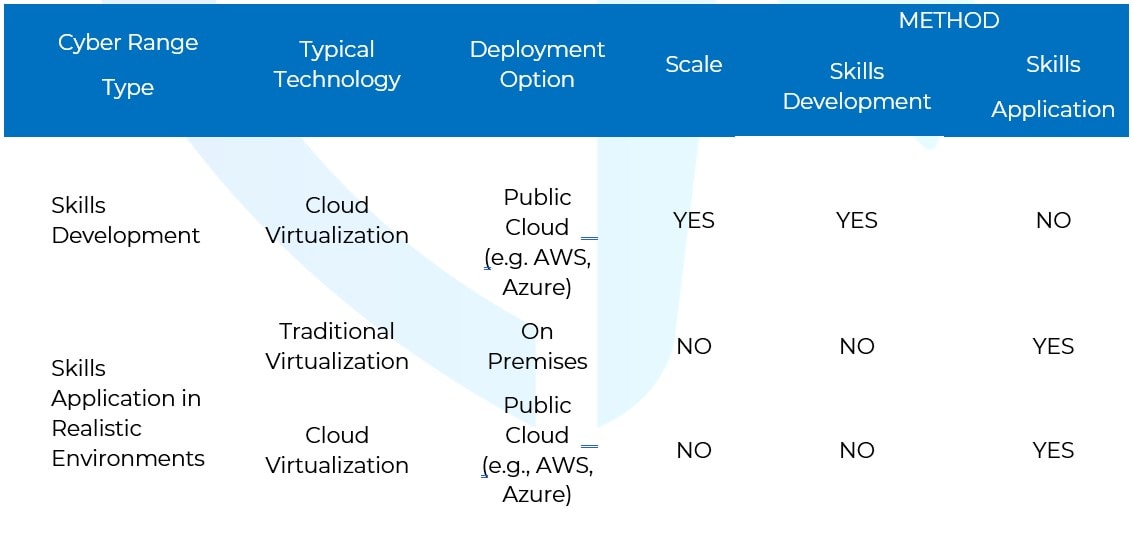
As we can see, only ranges based on cloud technology can offer cost-effective scalability solutions albeit limited to skills development (we discuss more on this later on). However, since such ranges are mostly developed on public cloud providers, they do not offer on-premise deployments and, when they do, they can be very costly, which greatly affects the return on investment for the client organization.
On the other hand, cyber ranges built on traditional technology are usually associated to on-premise deployments with a set number of realistic scenarios that are designed to be booted once by the trainer and not started dynamically by any number of users.
In fact, traditional virtualization technology has been developed with data centres in mind, to provide organizations with the ability to manage hundreds of servers much more efficiently and cost effectively. The main use case for traditional virtualization is to have servers running (boot once and re-boot when needed) and not to have a large number of both servers and clients dynamically boot, shut down, delete, configure on demand etc., which is instead required for flexible and dynamic delivery of experiential training.
Cloud-Based Cyber Ranges vs Cloud Cyber Ranges
The widespread adoption of the word ‘cloud’ with its alas improper use has confused matters when it comes to cyber ranges. A cloud cyber range is a cyber range available through the cloud, normally a public one. A cloud-based cyber range is instead a cyber range built on cloud technology, which does not necessarily mean that the range is available through the cloud, although that is also likely. The key here is to focus on the underlying technology used for the development of the range.
Cloud-technology is the key technology that can effectively address the scale aspect of the security training. While building on conventional virtualization, cloud virtualization abstracts the underlying physical resources across an entire infrastructure (RAM, storage, network, etc.) and makes them available transparently to end-users.
Cloud Technology and Orchestration
Orchestration is the automated configuration, coordination, and management of computer systems and software. In relation to cyber ranges and to virtualization technologies, orchestration refers to the technology responsible for the creation of automation workflows including the mass configuration, creation, modification and deletion of virtual machines, self-provisioning, and automation of tasks between the virtual infrastructure and other cyber range components or other systems interfacing with the cyber range.
Cyber range orchestration greatly affects the scalability, usability and cost of using a cyber range as well as the support for specific use cases, such as the ability to automatically schedule attacks and user activity simulation, events injection and more.
The following table summarizes the orchestration capabilities of the two different types of cyber ranges.
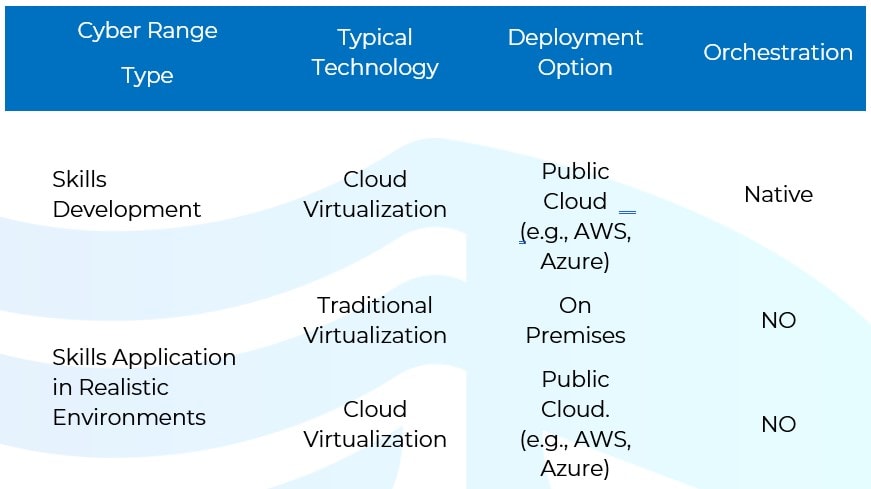
While orchestration is a native functionality of cloud technology, offered by public cloud providers, it is interesting to see that, when it comes to the management of realistic simulation environments, such capability needs to be further developed by the cyber range vendor. This latter challenge is even for those vendors that use traditional virtualization technology where orchestration is absent by default. What that means is that, while it is easy to provide users with access to click-and-play skills development labs, which boot one or two virtual machines, when it comes to enabling users to boot complex realistic environments and to set them up for use by a dynamic number of users and/or teams, this is not so straightforward and the process must be managed by the vendor or by a trainer at best. This limitation affects both the scalability and the cost of being able to run realistic simulations, which is the second most fundamental aspect of experiential learning.
This is the very reason why cyber ranges offering realistic simulation capabilities on public clouds cannot easily scale up and commoditize their service offering beyond the skills development aspect. Another way of explaining this point is that cyber ranges providing realistic simulation environments can be compared to flight simulators. However, flight simulators cost millions of dollars and are used to train thousands of aircraft pilots, while the industry needs a cost-effective solution to train millions of cyber security professionals.
The Next-Generation Cyber Range Solution
When talking about cyber ranges and trying to understand the difference between traditional, old-generation cyber ranges and next-generation cyber ranges, the key is in the ability of a cyber range to address both aspects of scaling and experiential learning methods in a manner that is cost-effective for the organization.
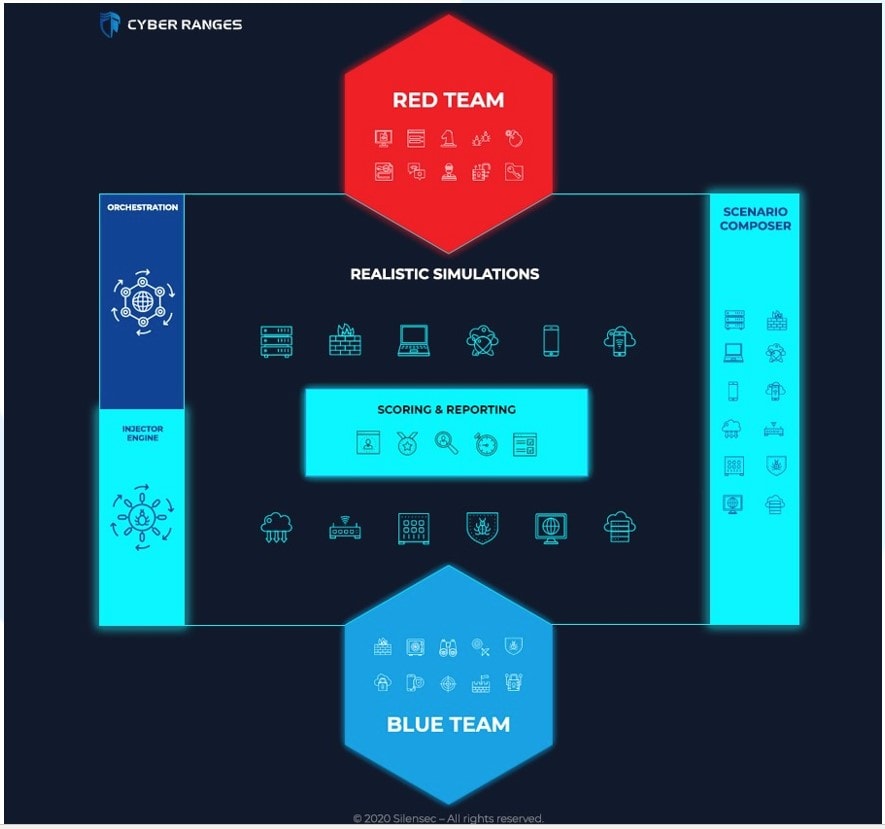
Next-generation cyber ranges address both scale and method, simultaneously. Next-generation cyber ranges come with the following characteristics:
- High level of orchestration to scale both skills development and application of those skills in realistic simulation environments
- Integrated functionalities to support different use cases
- User Activity and Attack Simulation
- Ability to easily add experiential learning content for both the development of skills and the application of such skills in realistic simulation environments
- Ability to be deployed on cloud or on premises with comparable costs
- Click-and-play ease of use even for complex realistic simulation environments
- Integrated learning management system to manage users’ upskilling progression and experience.
Measuring the Cyber Range ROI
When it comes to measuring the return on investment of a cyber range, it is important to understand how that cyber range will meet today’s requirements while providing the flexibility to address tomorrow’s requirements and changes in cyber threats and technologies.
We have already established that experiential learning requires both the development of skills and the application of those skills in realistic simulation environments. However, below are some questions that help gauge the costing of a cyber range:
- Can your cyber range provide both skills development and application of such skills in realistic simulation environments?
- Is the development of new realistic environments offered only as a service by the vendor or can it be easily carried out in-house on your cyber range?
- How easily can you integrate new technologies and attack simulations inside your range?
- Does your range integrate with your existing learning management system?
- Can you use the range for implementing different use cases?
If most of your answers to the above include the involvement of your range vendor you are clearly not dealing with a next-generation cyber range and your costs will surely be attached to the services delivered by the vendor.
Think of your cyber range as a game console. You may buy that console today because you like the games that come with it, but in a few months down the line you may want to play new games and you may want to support many more players. It is important to factor in the cost of new games development, licenses of new players and additional hardware requirements to scale over time. Next-generation cyber ranges are the game console of the future.
Conclusions
A cyber range is often compared to a flight simulator. However, flight simulators cost millions of dollars and are used to train thousands of aircraft pilots, while governments and businesses look for a cost-effective solution to train millions of cyber security professionals.
Next-generation cyber ranges are the sought-after solution: they can address both dimensions – scale and method – of the security skills gap, and make use of suitably engaging experiential content supplied by vendors off the shelf as well as custom-designed and built, directly in-house, by the same organization that needs to train its security professionals and confidentially test its own cyber resilience.

