Cyber Range technology – Over last two years, the cyber security market has watched the introduction of a larger and larger number of cyber range technologies, products and related services.
When looking at cyber ranges it is easy to recognize the typical behaviour captured by the famous diffusion and innovation model firstly described by Prof. Everett Rogers in 1962 and used over the years to describe how novel ideas and technology spread and are adopted by consumers.
Understanding what a cyber range is and where the market is today with regards to the Cyber Range Technologyspread and adoption of cyber ranges is key to ensuring successful investments while reducing failed expectations.
In this article, I have outlined what a cyber range is, the current state of the art and limitations and what I expect cyber ranges to evolve into in the coming years.
What is a Cyber Range?
For many years cyber ranges have been defined as an interactive, simulated representation of ICT and/or OT environments, including the simulation of Internet services for the primary purpose of security testing. However, with the introduction of Cyber as a separate Military domain — the US Defense Department officially incorporated cyber as a fifth military dimension in 2011, while NATO acknowledged cyberspace as an operational domain only later in 2016 — all nations from around the world have been increasingly developing cyber security strategies, including the development and acquisition of cyber capabilities. These can be defined as the resources and assets available to a State for the purposes of resisting or projecting influence through cyberspace. In such a context, the field of application for cyber ranges has grown to include security education (from high-schools to universities), security training and skills assessment, development and assessment of cyber resilience and also the development of digital dexterity, which Gartner defines as “the ability and desire to exploit existing and emerging technologies for business outcomes”1.
It is no surprise then that the early cyber ranges were developed in the military domain to serve a very specific user group and very specific use cases. However, with the number of cyber range applications and scalability requirements increasing, it soon became clear that the usability of a cyber range was closely coupled with a set of additional functionalities that go far beyond the original ability to provide a simulated representation of ICT/OT infrastructure.
To that extent, in the past two years, the market has been referring to what is now defined as “next-generation cyber ranges”.
The first definition of a next-generation cyber range was coined by the European Cyber Security Organization (ECSO)2, which defines a cyber range as:
“a platform for the development, delivery and use of interactive simulation environments. A simulation environment is a representation of an organisation’s ICT, OT, mobile and physical systems, applications and infrastructures, including the simulation of attacks, users and their activities and of any other Internet, public or third-party services which the simulated environment may depend upon. A cyber range includes a combination of core technologies for the realisation and use of the simulation environment and of additional components which are, in turn, desirable or required for achieving specific cyber range use cases”
Compared to a traditional cyber range, a next-generation cyber range is therefore presented as a platform which includes the ability to simulate ICT/OT environments, but it also includes the set of integrated functionalities that help in the use of the simulation environments. How easy it is to dynamically create different simulation environments and the breadth of functionalities offered will then vary across different cyber range products. The following figure, from the ECSO paper on cyber ranges clearly illustrates the concept of the next-generation cyber ranges.
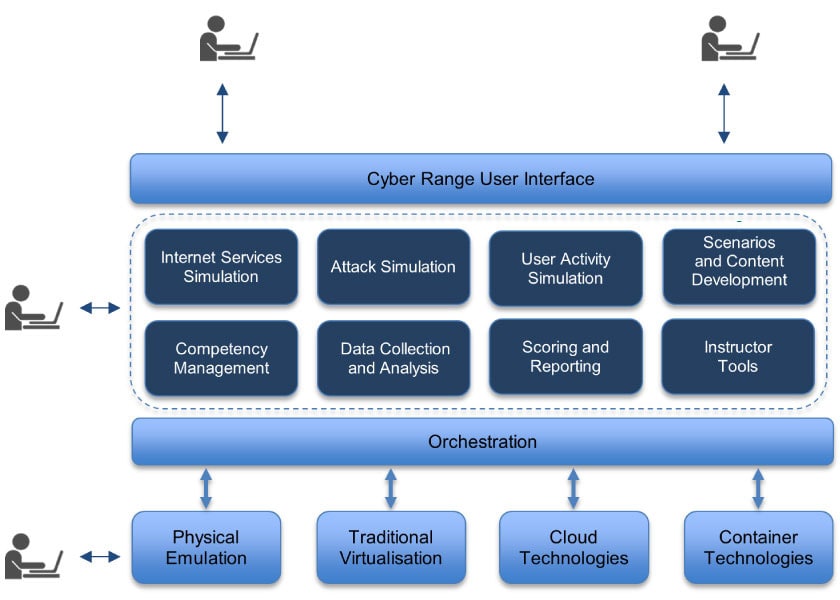
Figure 1 – The concept of the next-generation cyber ranges
Cyber Range Technologies
When talking about cyber range technologies, the focus of the discussion is mostly around virtualisation since it is the only technology that allows the creation of cost-effective and efficient simulation environments. Naturally, not everything can be simulated by using virtualisation technologies and some parts of a simulation environment may indeed require physical components, such as in the simulation of industrial control systems. Broadly speaking, cyber ranges can be divided into two types, based on the virtualization technologies used to develop them:
- Conventional Cyber Ranges – These are cyber ranges based on conventional virtualisation, including traditional hypervisor-based virtualisation and container technology. Many cyber ranges rely on one or the other, or a combination of the two. Cyber ranges built on traditional virtualisation are not characterized by a strong level of orchestration and are usually associated to physical cyber range locations with large virtualisation deployments. For the same reasons, conventional cyber ranges are not typically referred to as next-generation cyber ranges.
- Cloud-based Cyber Ranges – These are cyber ranges based on cloud technology. There are currently too many types of such cyber ranges:
- Public Cloud Cyber Ranges – These are cyber ranges developed on public cloud providers such as AWS, MS Azure or Google. They are tightly integrated with the public cloud providers and only available as a cloud service without an on-premise option.
- Private Cloud Cyber Ranges – These are ranges that do not rely on public cloud providers but are developed on similar cloud technologies, thus giving the flexibility to be offered as a cloud service or deployed on premise.
The inherent support for orchestration, dynamic configurations, increased efficiency and scalability makes cloud-based technology the preferred choice for next-generation cyber ranges.
The Rise of Public Cloud Ranges
Much of the market knowledge about cyber ranges today is based on cyber ranges developed on public cloud providers. This is both good and bad and it deserves special attention in order to enable users to have a clear understanding of what a cyber range is in order to avoid failed expectations.
Most providers of cloud-based cyber ranges today focus on one specific use case, which is that of providing flexible hands-on learning environments where users can go through click-and-play scenarios addressing a range of different security domains, from ethical hacking to incident response and malware analysis. While promoted as cyber ranges, such providers do no provide all the functionalities required by a user to create custom simulation environments and to use those environments for bespoke use cases. What you see is what you get, and users of such cyber ranges are limited to what is available on the library exposed by the cyber range provider. Furthermore, most of such cyber ranges are reliant on the public cloud providers and the API exposed by those providers and they cannot be deployed on premise. Furthermore, any customization is tied to the service provider giving organization little or no freedom to operate the proposed cyber range.
In line with the definition of next-generation cyber ranges, online cloud-based ranges based on public cloud providers do not represent a cyber range per se and only offer a specific use case of cyber ranges. Furthermore, such cyber ranges cannot be used where there are limits or constraints, by policy or regulation, which prohibit the use of public cloud for the storage of personal data.
Managing Expectations About Cyber Ranges
The following figure illustrates the diffusion and innovation model applied to cyber ranges. As with any such model, diffusion and adoption of new ideas and technology are characterized by specific technology triggers. With regards to cyber ranges, the key technology triggers that have sparked the spread of cyber range products are two: cloud technology and attack simulation.
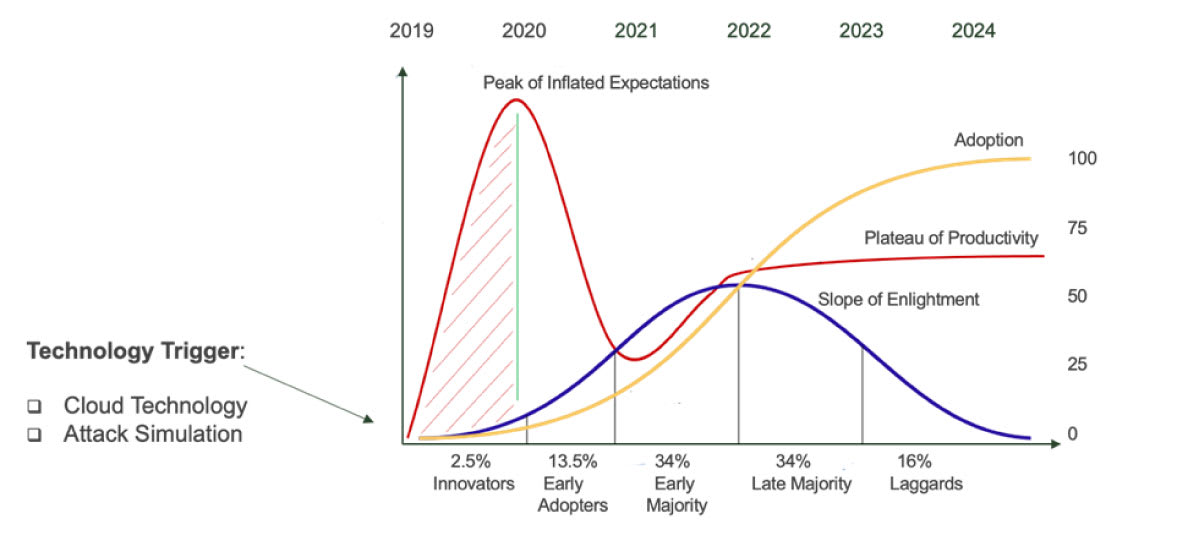
The diffusion and innovation model applied to cyber ranges
As cloud technology has become more mature and commoditized, many cyber range vendors have begun using it to build their cyber ranges, mostly using public cloud providers. That has made the access to experiential training much more widely available and a reduced cost. Agent-based attack simulation has also seen incredible advances in recent years and has introduced a new security product domain called breach-and-attack simulation. Agent-based attack simulation has introduced new capabilities to cyber ranges to simulate attacks, users, APTs and more. However, the true benefit of attack simulation is only achieved through its integration with the cyber range platform and not as an add-on functionality.
When it comes to managing expectations and getting the true value from a cyber range, the key point to focus on, within the diffusion and innovation model, is the “Peak of Inflated Expectations”. As many of the original cyber ranges were built on conventional virtualization technologies, they were also the first to appear on the market to meet the growing demand. However, such cyber ranges lack the key integrated functionalities that are expected from a next-generation cyber range. Main shortfalls include lack of orchestration, lack of integrated attack simulation, lack of integration with competency frameworks and limited or non-existing authoring capabilities. Specifically, while many cyber ranges may market and advertise such functionalities, those functionalities are built as an add-on on top of a conventional virtualization technology and not integrated into a single platform. Such lack of integration is reflected on the inability of those cyber ranges to expose such functionalities to the end user, who is then forced to go through the vendor thus affecting costs and usability.
Next-generation cyber ranges instead, which have been introduced in more recent time have been built from the ground up as a platform integrating all the required functionalities to meet different use cases, exposing all the required to the functionalities to the end users.
Concluding Remarks
As of today, the cyber range market is broadly divided into three categories:
- cyber ranges built on conventional virtualization;
- online cyber ranges built on public cloud providers;
- cyber ranges built from the ground up as a platform and using cloud technology.
The first type, also the first to market, provides limited flexibility and functionalities with an expensive price tag. The second type provides a good return on investment for a specific use case. The latter types, also called next-generation cyber ranges bring organizations the flexibility and functionalities required, together with the pathway for controlled and future-proof investments.
The next two years will see the development of next-generation cyber ranges towards a much more commoditized model, including native integration with public providers introducing hybrid cyber ranges, which will bring the ultimate flexibility in terms of functionality, scalability and costing models. So invest wisely on both the product, its vendor and its partner ecosystem.
Author: Dr. Al Graziano, CEO, Silensec | CYBER RANGES
Co-chair, ECSO WG5 on Education, Training, Awareness and Cyber Ranges, and SWG5.1 on Cyber Range Environments and Technical Exercises
References
- Gartner (2020), Digital Dexterity, at the Gartner Digital Workplace Summit
- ECSO (2020) Understanding Cyber Ranges: From Hype to Reality

